06.Security
1) View Certificate Details
2) Certificates API
3) KubeConfig
4) Role Based Access Controls
5) Cluster Roles
6) Service Accounts
7) Image Security
8) Security Contexts
9) Network Policies
01. How many Service Accounts exist in the default namespace?
ask : 1
root@controlplane:/# k get serviceaccount
NAME SECRETS AGE
default 1 23m
02. What is the secret token used by the default service account?
ask : default-token-hznd7
root@controlplane:/# k get secrets
NAME TYPE DATA AGE
default-token-hznd7 kubernetes.io/service-account-token 3 24m03. We just deployed the Dashboard application. Inspect the deployment.
What is the image used by the deployment?
ask : gcr.io/kodekloud/customimage/my-kubernetes-dashboard
root@controlplane:/# k describe deployments web-dashboard
Name: web-dashboard
Namespace: default
CreationTimestamp: Thu, 27 Jan 2022 02:36:25 +0000
Labels: <none>
Annotations: deployment.kubernetes.io/revision: 1
Selector: name=web-dashboard
Replicas: 1 desired | 1 updated | 1 total | 1 available | 0 unavailable
StrategyType: RollingUpdate
MinReadySeconds: 0
RollingUpdateStrategy: 25% max unavailable, 25% max surge
Pod Template:
Labels: name=web-dashboard
Containers:
web-dashboard:
Image: gcr.io/kodekloud/customimage/my-kubernetes-dashboard
Port: 8080/TCP
Host Port: 0/TCP
Environment:
PYTHONUNBUFFERED: 1
Mounts: <none>
Volumes: <none>
Conditions:
Type Status Reason
---- ------ ------
Available True MinimumReplicasAvailable
Progressing True NewReplicaSetAvailable
OldReplicaSets: <none>
NewReplicaSet: web-dashboard-5899cf7849 (1/1 replicas created)
Events:
Type Reason Age From Message
---- ------ ---- ---- -------
Normal ScalingReplicaSet 72s deployment-controller Scaled up replica set web-dashboard-5899cf7849 to 1
04. Wait for the deployment to be ready.
Access the custom-dashboard by clicking on the link to dashboard portal.
대시보드 포털 링크를 클릭하여 맞춤형 대시보드에 액세스합니다.
05. What is the state of the dashboard? Have the pod details loaded successfully?

ask : fail
06. What type of account does the Dashboard application use to query the Kubernetes API?
대시보드 애플리케이션은 Kubernetes API를 쿼리하는 데 어떤 유형의 계정을 사용합니까?
1) Service Account
2) LDAP Account
3) User Account
4) OAuth Account
07. Which account does the Dashboard application use to query the Kubernetes API?
대시보드 애플리케이션은 Kubernetes API를 쿼리하는 데 어떤 계정을 사용합니까?
1) Kube-admin
2) Admin
3) Administrator
4) Default
08. Inspect the Dashboard Application POD and identify the Service Account mounted on it.
대시보드 애플리케이션 POD를 검사하고 여기에 탑재된 서비스 계정을 식별합니다. (????)
1) dashboard-sa
2) service-account
3) default
09. At what location is the ServiceAccount credentials available within the pod?
포드 내에서 ServiceAccount 자격 증명을 사용할 수 있는 위치는 어디입니까?
1) /var/run/token
2) /var/run/secrets
3) /opt/run/secrets
4) /etc/run/secrets
root@controlplane:/# k describe pod web-dashboard-5899cf7849-lzct4 | grep service
/var/run/secrets/kubernetes.io/serviceaccount from default-token-hznd7 (ro)
10. The application needs a ServiceAccount with the Right permissions to be created to authenticate to Kubernetes.
The 'default' ServiceAccount has limited access.
Create a new ServiceAccount named 'dashboard-sa'.
- Secret Name: dashboard-sa
kubectl create serviceaccount dashboard-sa
11. The application needs a ServiceAccount with the Right permissions
to be created to authenticate to Kubernetes.
The 'default' ServiceAccount has limited access.
Create a new ServiceAccount named 'dashboard-sa'.
| 애플리케이션은 Kubernetes에 인증하기 위해 생성할 권한이 있는 ServiceAccount가 필요합니다. '기본' ServiceAccount에는 액세스가 제한되어 있습니다. 'dashboard-sa'라는 새 ServiceAccount를 만듭니다. |
- Secret Name: dashboard-sa
root@controlplane:/# kubectl create serviceaccount dashboard-sa
serviceaccount/dashboard-sa created
11. We just added additional permissions for the newly created dashboard-sa account using RBAC.
방금 RBAC를 사용하여 새로 생성된 Dashboard-sa 계정에 대한 추가 권한을 추가했습니다.
If you are interested checkout the files used to configure RBAC at /var/rbac.
관심이 있으시면 /var/rbac에서 RBAC를 구성하는 데 사용되는 파일을 확인하십시오.
We will discuss RBAC in a separate section.
RBAC에 대해서는 별도의 섹션에서 논의할 것입니다.
# dashboard-sa-role-binding.yaml
---
kind: RoleBinding
apiVersion: rbac.authorization.k8s.io/v1
metadata:
name: read-pods
namespace: default
subjects:
- kind: ServiceAccount
name: dashboard-sa # Name is case sensitive
namespace: default
roleRef:
kind: Role #this must be Role or ClusterRole
name: pod-reader # this must match the name of the Role or ClusterRole you wish to bind to
apiGroup: rbac.authorization.k8s.io# pod-reader-role.yaml
---
kind: Role
apiVersion: rbac.authorization.k8s.io/v1
metadata:
namespace: default
name: pod-reader
rules:
- apiGroups:
- ''
resources:
- pods
verbs:
- get
- watch
- list12. Enter the access token in the UI of the dashboard application.
대시보드 애플리케이션의 UI에 액세스 토큰을 입력합니다.
| Enter the access token in the UI of the dashboard application. Click Load Dashboard button to load Dashboard Retrieve the Authorization token for the newly created service account , copy it and paste it into the token field of the UI.
To do this, run kubectl describe against the secret created for the dashboard-sa service account, copy the token and paste it in the UI. |
| 대시보드 애플리케이션의 UI에 액세스 토큰을 입력합니다. 대시보드 로드 버튼을 클릭하여 대시보드 로드 새로 생성된 서비스 계정에 대한 인증 토큰을 검색하고 복사하여 UI의 토큰 필드에 붙여넣습니다. 이렇게 하려면 대시보드-sa 서비스 계정에 대해 생성된 비밀에 대해 kubectl describe를 실행하고 토큰을 복사하여 UI에 붙여넣습니다. |
root@controlplane:/var/rbac# k get secrets
NAME TYPE DATA AGE
dashboard-sa-token-xcfv9 kubernetes.io/service-account-token 3 8m9s
default-token-hznd7 kubernetes.io/service-account-token 3 57m
root@controlplane:/var/rbac# k describe secrets dashboard-sa-token-xcfv9
Name: dashboard-sa-token-xcfv9
Namespace: default
Labels: <none>
Annotations: kubernetes.io/service-account.name: dashboard-sa
kubernetes.io/service-account.uid: 301d27cd-81af-49ee-9b8f-7334a8982e24
Type: kubernetes.io/service-account-token
Data
====
ca.crt: 1066 bytes
namespace: 7 bytes
token: eyJhbGciOiJSUzI1NiIsImtpZCI6Ijc3ZjVLenlGMGtnVlBWOEtBWUFlRmFIbFcwZWZobVNia3dhOWU4QV9neG8ifQ.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJkZWZhdWx0Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9zZWNyZXQubmFtZSI6ImRhc2hib2FyZC1zYS10b2tlbi14Y2Z2OSIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50Lm5hbWUiOiJkYXNoYm9hcmQtc2EiLCJrdWJlcm5ldGVzLmlvL3NlcnZpY2VhY2NvdW50L3NlcnZpY2UtYWNjb3VudC51aWQiOiIzMDFkMjdjZC04MWFmLTQ5ZWUtOWI4Zi03MzM0YTg5ODJlMjQiLCJzdWIiOiJzeXN0ZW06c2VydmljZWFjY291bnQ6ZGVmYXVsdDpkYXNoYm9hcmQtc2EifQ.eMwDgdackkcrucQ_jQPtqIW7QTgkPC3PgKVfXSEm1hE9qB712PLv4OauHk5UBQzkr3AZtLCeB5LujUWSfmLl0wmrPBrb-7KldQLuHNwGHUgMpK5BjND1_M7nQMi90BHlckxSk_q06a62JuZzBobtYjGaKNPQynzN15YYoxDmbqAyxxu0BegNNMGSy-hfu2M8WHVF9jrRAGMDmD2zJlfhp2yIoT5KfI-fjtHLcFJP_9be4-hNz00BnIvJU6ztjp0SOPc4JJpGTSuRvRFuidftFAShrdCpjzDcPvl6nOyE75wiN_kO4IRwJ-Cf06MhrQ-tOEdSmfHF0zWlBeMcisH1bQ

13. You shouldn't have to copy and paste the token each time.
The Dashboard application is programmed to read token from the secret mount location.
However currently, the 'default' service account is mounted.
Update the deployment to use the newly created ServiceAccount
Edit the deployment to change ServiceAccount from 'default' to 'dashboard-sa'
| 매번 토큰을 복사하여 붙여넣을 필요가 없습니다. 대시보드 애플리케이션은 비밀 마운트 위치에서 토큰을 읽도록 프로그래밍되었습니다. 그러나 현재 '기본' 서비스 계정이 탑재되어 있습니다. 새로 생성된 ServiceAccount를 사용하도록 배포 업데이트 ServiceAccount를 'default'에서 'dashboard-sa'로 변경하도록 배포를 편집합니다. |
- Deployment name: web-dashboard
- Service Account: dashboard-sa
- Deployment Ready
# step 01
k edit deployment.apps/web-dashboard
# step 02
spec 하위에
serviceAccount: default
serviceAccountName: dashboard-sa
두개 추가후 저장Use following YAML file:
apiVersion: apps/v1
kind: Deployment
metadata:
name: web-dashboard
namespace: default
spec:
replicas: 1
selector:
matchLabels:
name: web-dashboard
strategy:
rollingUpdate:
maxSurge: 25%
maxUnavailable: 25%
type: RollingUpdate
template:
metadata:
creationTimestamp: null
labels:
name: web-dashboard
spec:
serviceAccountName: dashboard-sa
containers:
- image: gcr.io/kodekloud/customimage/my-kubernetes-dashboard
imagePullPolicy: Always
name: web-dashboard
ports:
- containerPort: 8080
protocol: TCP
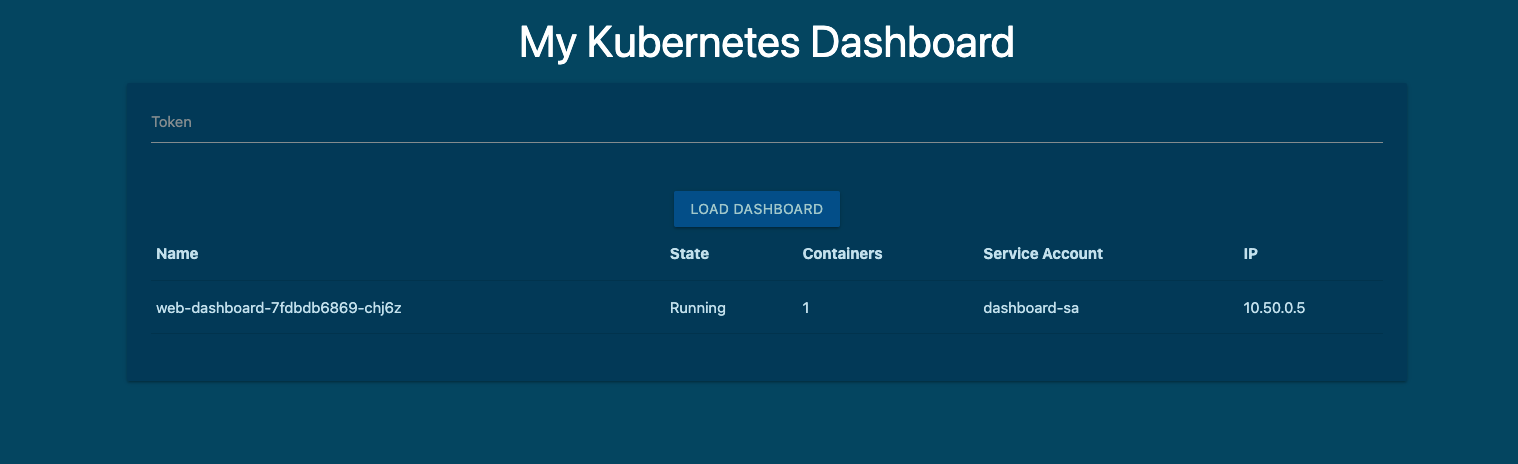
14. Refresh the Dashboard application UI and you should now see the PODs listed automatically.
This time you shouldn't have to put in the token manually
https://kubernetes.io/docs/tasks/configure-pod-container/configure-service-account/
Configure Service Accounts for Pods
A service account provides an identity for processes that run in a Pod. Note: This document is a user introduction to Service Accounts and describes how service accounts behave in a cluster set up as recommended by the Kubernetes project. Your cluster admi
kubernetes.io
'CKA (Certified Kubernetes Administrator) > Kode Kloud' 카테고리의 다른 글
| 06.Security - Security Contexts (0) | 2022.01.27 |
|---|---|
| 06.Security - Image Security (0) | 2022.01.27 |
| 06. Security - ClusterRoles (0) | 2022.01.26 |
| 10.Troubleshooting - Application Failure (0) | 2022.01.26 |
| 06.Security - Role Based Access Controls (0) | 2022.01.25 |